
Computer Systems: A Programmer's Perspective (3rd Edition)
3rd Edition
ISBN: 9780134092669
Author: Bryant, Randal E. Bryant, David R. O'Hallaron, David R., Randal E.; O'Hallaron, Bryant/O'hallaron
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Textbook Question
Chapter 10.8, Problem 10.2PP
Practice Problem 10.2 (solution page 915)
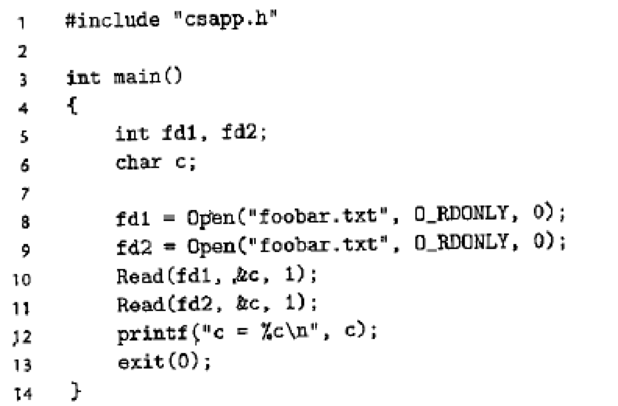
Suppose the disk file foobar.txt consists of the six ASCII characters foobar. Then what is the output of the following
Expert Solution & Answer
Want to see the full answer?
Check out a sample textbook solution
Students have asked these similar questions
(c) Write a Haskell program that:
• Reads two files, called "input1.txt" and "input2.txt".
• Interleaves the lines of the two files.
• Writes the result to a file called "output12.txt" .
You may make use of any functions in the Reference (pp5-7).
[Python (py3)]
Using import numpy as np, import sys and def functions, create a code that accepts input from a text file, solves matrix operations (add, scalar multiply, multiply, or transpose), and prints output to a text file. Note: If Matrix A and Matrix B are ordered to be added but the dimension of Matrix A is not equal to the dimension of Matrix B, print "Matrix addition cannot be performed; dimensions are unequal."Note: If Matrix A and Matrix B are ordered to be multiplied but the number of columns of Matrix A is not equal to the number of rows of Matrix B, print "Matrix multiplication cannot be performed; number of columns of Matrix A is not equal to number of rows of Matrix B."Please annotate the significant parts.
Format of the input from text file:First Line: type of operation (add, multiply, scalmultiply, or transpose)Second Line: matrix A dimension (example: if 3 rows and 2 columns, type 3 2)Third Line: matrix A elementsFourth Line: matrix B dimension (or the scalar number…
(python)
10. Create a function based on the following information:
Your mission is to encrypt a secret message (text only, without special chars like "!", "&", "?" etc.) using Caesar cipher where each letter of input text is replaced by another that stands at a fixed distance. For example ("a b c", 3) == "d e f"
Input: A secret message as a string (lowercase letters only and white spaces) and number to move text
Output: The same string, but encrypted
Return: The same string, but encrypted
Chapter 10 Solutions
Computer Systems: A Programmer's Perspective (3rd Edition)
Ch. 10.3 - Prob. 10.1PPCh. 10.8 - Practice Problem 10.2 (solution page 915) Suppose...Ch. 10.8 - Practice Problem 10.3 (solution page 915) As...Ch. 10.9 - Prob. 10.4PPCh. 10.9 - Practice Problem 10.5 (solution page 916) Assuming...Ch. 10 - Prob. 10.6HWCh. 10 - Prob. 10.7HWCh. 10 - Write a version of the statcheck program in Figure...Ch. 10 - Consider the following invocation of the...Ch. 10 - Prob. 10.10HW
Additional Engineering Textbook Solutions
Find more solutions based on key concepts
Contrast the following terms: chief data officer; DBA data administration: database administration open source ...
Modern Database Management (12th Edition)
(Pattern matching) Write a program that prompts the user to enter two strings and tests whether the second stri...
Introduction to Java Programming and Data Structures, Comprehensive Version (11th Edition)
Practice Program 5.4 asked you to define Trivia class that contained strings representing a trivia question and...
Java: An Introduction to Problem Solving and Programming (8th Edition)
Suppose that at time t=0, half of a logistic population of l00,000 persons have heard a certain rumor, and that...
Differential Equations: Computing and Modeling (5th Edition), Edwards, Penney & Calvis
Describe the purpose of the access key attribute and how it supports accessibility.
Web Development and Design Foundations with HTML5 (8th Edition)
Suppose a machine language is designed with an op-code field of 4 bits. How many different instruction types ca...
Computer Science: An Overview (13th Edition) (What's New in Computer Science)
Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Huffman Code[Problem Description]For an English article, the frequency of occurrence of 26 lowercase letters is counted, and then they are encoded by Hoffman code.[Basic Requirements]1) Read the original text file from the file and display the text on the screen..2) Output the number of occurrences of 26 English lowercase letters, and the corresponding Hoffman code... Below is the data to be displayed At present, most of the dynamic sign language recognition is only for sign language words,the continuous sign language sentence recognition research and the corresponding results are less, because the segmentation of such sentence is very difficult. In this paper, a sign languagesentence recognition algorithm is proposed based on weighted key frames. Key frames can be regardedas the basic unit of sign word, therefore, according to the key frames we can get related vocabularies, and thus we can further organize these vocabularies into meaningful sentence. Such work can avoid the…arrow_forwardI need help with this: (Address book) Write a program that stores, retrieves, adds, and updates addresses as shown in Figure 17.20. Use a fixed-length string for storing each attribute in the address. Use random access file for reading and writing an address. Assume that the size of name, street, city, and zip is 32, 32, 20, 2, 5 chars, respectively.arrow_forwardProblem 2 (Cipher module)• Create a Python file named cipher_module.py with functions to encode and decodestring inputs using the basic Caesar cipher (see here for more informationhttps://en.wikipedia.org/wiki/Caesar_cipher). This cipher is a basic encryptiontechnique that supports encoding and decoding operations on strings.• The encoding operation replaces each character in a string with another charactersome fixed number (shift) of positions down the ASCII table. The string can beencoded using any characters on the ASCII table and no need to use the circular list(where ‘Z’ is followed by ‘A’) image shown below. Your module must have a functionnamed encode() that takes a string and an integer shift (can be positive or negative)as parameters and returns the encoded string using the shift value. This module must Page 3 of 4also have a second function name decode() that takes an encoded string and aninteger shift as parameters and returns the decoded string. The decoding…arrow_forward
- 10:22 Q4: [Principal Component Analysis] a. Write the pseudo-code of the Principal Component Analysis algorithm b. A study revels that the average temperature and energy demanded are correlated in nature. The study help to forecast the energy demand as a function of the average temperature. The average temperature let x °F and the day's energy demand denoted as 'y' (MWH) were recorded. Compute the principal component of the given data using PCA Algorithm as a function of Covariance matrix, Eigen values and eigenvectors of the covariance matrix, and Feature vectors Q6: [Aprori Algorithm] a. b. Observation No Average Temperature (X) Energy Demand (Y) 1 69 146 2 of 4 Q5: [Search Algorithm] a. Write the pseudo-code of the following search algorithm i. Uniform cost search II. Iterative Deepening Search b. Discuss the working principle, strength, and limitation of the following search algorithm i. Uniform cost search ii. Iterative Deepening Search C. Consider the following initial state of…arrow_forwardHuffman Code[Problem Description]For an English article, the frequency of occurrence of 26 lowercase letters is counted, and then they are encoded by Hoffman code.[Basic Requirements]1) Read the original text file from the file and display the text on the screen..2) Output the number of occurrences of 26 English lowercase letters, and the corresponding Hoffman code... HERE IS MY original TEXT to be displayed.. At present, most of the dynamic sign language recognition is only for sign language words,the continuous sign language sentence recognition research and the corresponding resultsare less, because the segmentation of such sentence is very difficult. In this paper, a sign languagesentence recognition algorithm is proposed based on weighted key frames. Key frames can be regardedas the basic unit of sign word, therefore, according to the key frames we can get related vocabularies,and thus we can further organize these vocabularies into…arrow_forwardProblem 2 Mr. Sulaiman AlHarthy is having 13 shops for selling fruits all over Oman. The daily sales from all the shops have been recorded in a text file called sales.txt. Mr. Sulaiman wants to know the total sales after discarding baise from each shop's sales amount. [Hint: sales amount in any shop always between 1 to 4 digits in OMR excluding basise] Your program must be menu driven and robust. The following are the tasks to be programmed. i) Write a function to read the given text file sales.txt and extract OMRS after discarding the digits after decimal point, including the decimal point and print the list of 13 sales amount. ii) Write a function to write the extracted sales data into another text file salesOMR.txt iii) Write a function to read from salesOMR.txt file and print the sum of sales. Handle FileNotFoundError exception in your code. The sample content of sales.txt is as follows: 500.335233.1235.12311.2342313.510231.12356.12022.220540.125122.4329.450463.19834.767arrow_forward
- H.W:- Find the value of Z Where Z=AX+BX+CX*DX, IF AX=4,BX=8,CX-2,DX-3 result in memory location (DS:1200H] IF DS=2000H? Alo Mor A+, 2000 Narrow_forwardProblem 2 Mr. Sulaiman AlIHarthy is having 13 shops for selling fruits all over Oman. The daily sales from all the shops have been recorded in a text file called sales.txt. Mr. Sulaiman wants to know the total sales after discarding baise from each shop's sales amount. [Hint: sales amount in any shop always between 1 to 4 digits in OMR excluding basise] Your program must be menu driven and robust. The following are the tasks to be programmed. i) Write a function to read the given text file sales.txt and extract OMRS after discarding the digits after decimal point, including the decimal point and print the list of 13 sales amount. ii) Write a function to write the extracted sales data into another text file salesOMR.txt iii) Write a function to read from salesOMR.txt file and print the sum of sales. Handle FileNotFoundError exception in your code. The sample content of sales.txt is as follows: 500.335233.1235.12311.2342313.510231.12356.12022.220540.125122.4329.450463.19834.767arrow_forwardComputer Science For LZ78: Task 1 - In order to compute the tuples of some text files, create a computer program using Java. Calculate how many tuples are computed. You should compress and decompress the text without any loss so check original text with decompressed text if they are same. Represent your tuples into bits’ representation and calculate for each file the compression ratio.Do above steps by proceeding assigned algorithm in reverse order. (From right to left) Regarding to above result: a) Compare the number of tuples b) Compare compression ratio (Use Huffman encoding Algorithm)arrow_forward
- Problem 3. (Encryption Program) Write a program called encrypt.py that accepts the public-key n (int) and e (int) as command-line arguments and a message to encrypt from standard input, encrypts each character in the message, and writes its fixed-width binary representation to standard output. 'A tuple is like a list, but is immutable. You create a tuple by enclosing comma-separated values within matched parentheses, eg, a = (1, 2, 3). If a is a tuple, a[i] is the ith element in it. 5 / 7 Project 4 (RSA Cryptosystem) >- "/workspace/project4 $ python3 encrypt.py 3599 1759 Cs110 000110000000010011010100001010100011001010100011001110000110010111100100 Directions: • Accept public-key n (int) and e (int) as command-line arguments. • Get the number of bits per character (call it width) needed for encryption, ie, number of bits needed to encode n. • Accept message to encrypt from standard input. • For each character c in message: - Use the built-in function ord() to turn c into an integer x.…arrow_forwardLaboratory Practice Task 5.5: Write a program that solves quadratic equation of the form ax2 + bx + c where a, band c are constant coefficients. Quadratic equation has two roots and they can be computed using the following formulas: root1 = -b + vb²- 4ac 2a root2 = -b - vb² - 4ac 2a FILENAME: PTASK5.5.cpp Note: Please copy the correct program. PROGRAMarrow_forward(5.1) In the context of designing a system that offers a file management capability, e.g., OneDrive, there are some constraints on the acceptable file names. The following three characters {*,$, :} in addition to spaces are not allowed in file names. If any of these four characters appears in a file name, it is replaced by a hyphen (-). Examples: "new file" → "new-file" "important$file" → "important-file" "abc$def gh:ij*klm.txt" → "abc-def-gh-ij-klm.txt" "exam.doc" →→ "exam.doc" i. Design an algorithm that takes a file name as a string and returns a modified name replacing the prohibited characters with hyphens. Use pseudocode to describe your algorithm. Define all operations that are used in your algorithm. ii. What is the runtime complexity of your algorithm?arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education
Instruction Format (With reference to address); Author: ChiragBhalodia;https://www.youtube.com/watch?v=lNdy8HREvgo;License: Standard YouTube License, CC-BY